Software developers have a supply chain security problem
[ad_1]
Log4j was the bucket of chilly drinking water that woke up most builders to their program supply chain protection difficulty.
We have invested decades in computer software making items and obsessing around our manufacturing natural environment. But we’re building on unpatched Jenkins packing containers sitting down underneath someone’s desk. We invest all this time preserving our runtimes, then deploy to them using novice tooling.
Our construct environments are not practically as secure as our generation environments.
Which is what led to a full ton of superior-profile attacks in the previous 12 months, from SolarWinds, to the Codecov attack, to the Travis CI techniques leak. We’ve gotten so excellent at protecting our infrastructure that attackers looked for an a lot easier way in, and located it in the doorways we have still left open up in the offer chain.
Can not get in via the perimeter safety? Just discover an open up supply dependency, or a library, and get in that way. Then pivot to all of the buyers. This is the modern-day computer software supply chain hack.
We want roots of belief for software
We have roots of have faith in for folks currently. We have two-factor authentication, we have identification systems. These are things to vouch for a person’s identity. And components has the very same issue. We have encryption keys. We have hardware we can trust hasn’t been tampered with when it boots up.
Even as web users we have roots of belief. We have URIs, URNs, and URLs—effectively the namespaces on the online that connect the identities, names, and areas of internet sites we are searching. SSL certificates tell our browsers that web pages are safe. DNS firewalls sit involving the user’s recursive resolvers to make certain our cache is not getting loaded with poor requests. All of this is taking place at the rear of the scenes, and has been incredibly powerful in supporting billions of world wide web consumers for many years.
But we really don’t have this for software package artifacts right now.
Builders believe in as well considerably implicitly
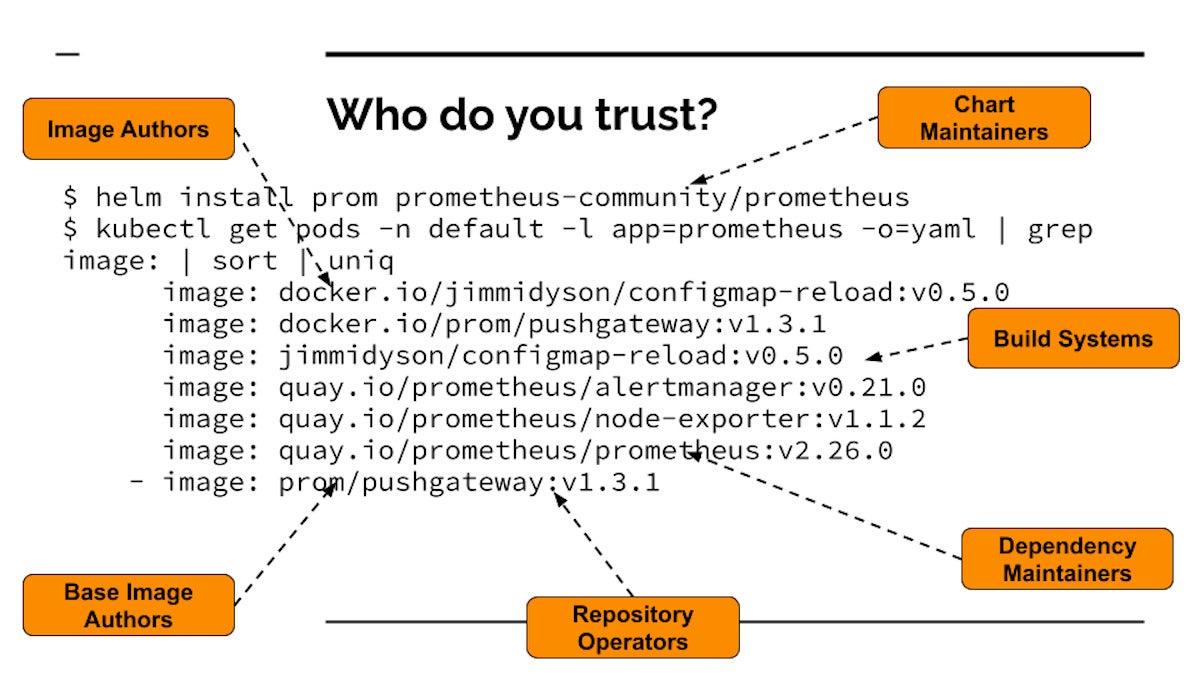
Just take an occasion as commonplace as putting in Prometheus (a well-liked open source observability challenge) from the Cloud Native Computing Basis (CNCF) artifact hub. If you do your Helm install and then glimpse at all the photographs that get pulled and start managing your cluster, you see quite a few container visuals that end up jogging from a uncomplicated set up. Builders are entrusting a total bunch of factors to a complete bunch of distinct persons and devices. Every single just one of these could be tampered with or attacked, or could be malicious.
 Dan Lorenc
Dan LorencThis is the opposite of Zero Trust—we’re trusting dozens of systems that we really don’t know nearly anything about. We do not know the authors, we never know if the code is destructive, and because each individual graphic has its individual artifacts, the complete supply chain is recursive. So we’re not only trusting the artifacts, but also the persons who trusted the dependencies of these artifacts.
We’re also trusting the folks who operate the repositories. So if the repository operators get compromised, now the compromisers are portion of your believe in circle. Any individual managing 1 of these repositories could modify a thing and attack you.
Then there is the construct units. Develop techniques can get attacked and insert destructive code. That’s precisely what occurred with SolarWinds. Even if you know and trust the operators of the photographs, and the individuals running the units that host the images, if these are constructed insecurely, then some malware can get inserted. And all over again it’s recursive all the way down. The dependency maintainers, the develop systems they use, the artifact managers that they are hosted on—they’re all undermined.
So when builders put in software program packages, there are a good deal of factors they are trusting implicitly, whether or not they suggest to have faith in them or not.
Application supply chain safety gotchas
The worst strategy you can have in software program provide chain safety is to do very little, which is what a lot of developers are executing now. They are allowing for just about anything to run on creation environments. If you have no stability around what artifacts can operate, then you have no notion wherever they arrived from. This is the worst of the worst. This is not spending consideration at all.
Enable-listing particular tags is the up coming degree up. If you go via some of the tutorials all-around greatest procedures with Kubernetes, this is fairly straightforward to established up. If you push all your visuals to a one spot, you can at least restrict items to that spot. That is way much better than executing almost nothing, but it is however not great, due to the fact then something that receives pushed there is now inside your have faith in circle, within that barbed wire fence, and that’s not truly Zero Rely on. Let-listing specific repositories has all the identical restrictions of let-listing certain tags.
Even the signing schemas in offer chain security are papering about the similar trouble. Anything at all that will get signed now will get to run, irrespective of where by it arrived from, which leads to tons of assaults tied to tricking an individual to indication the wrong issue, or currently being not able to revoke a certificate.
Time to get started inquiring the suitable thoughts
Let us say you are strolling down the sidewalk outdoors of your office environment, and you locate a USB thumb generate sitting on the floor. I hope everybody knows that you ought to definitely not take that push within your business and plug it into your workstation. Everyone in program ought to (rightly) be screaming, “No!” True assaults have happened this way, and safety orgs across the world hammer this warning into all staff as portion of coaching.
But for some purpose, we do not even pause to consider two times prior to operating docker pull or npm put in, even although these are arguably worse than plugging in a random USB adhere. Equally situations contain taking code from an individual you do not rely on and functioning it, but the Docker container or NPM package deal will eventually make it all the way into your production environment!
The essence of this offer chain safety evolution is that as an field we’re relocating absent from trusting where the software package artifacts appear from, and spending substantially additional time figuring out roots of believe in for what the artifact is.
Who printed this binary? How was it constructed? What version of the software was applied? What source was it developed from? Who signed off on this code? Was nearly anything tampered with? These are the right concerns to be inquiring.
Up coming 7 days, we’ll appear at the rapid-evolving open source landscape that is forming a new security stack for source chain security, and unpack critical principles developers need to have to understand—from roots of rely on, to provenance, to TPM (Dependable System Module) attestation.
Dan Lorenc is CEO and co-founder of Chainguard. Earlier he was workers software package engineer and guide for Google’s Open up Resource Stability Workforce (GOSST). He has launched assignments like Minikube, Skaffold, TektonCD, and Sigstore.
—
New Tech Discussion board gives a location to check out and focus on rising business technology in unprecedented depth and breadth. The collection is subjective, based on our decide of the systems we think to be critical and of finest interest to InfoWorld visitors. InfoWorld does not take promoting collateral for publication and reserves the suitable to edit all contributed content. Deliver all inquiries to [email protected].
Copyright © 2022 IDG Communications, Inc.
[ad_2]
Resource website link